What is TCP/IP?. 3
Subnet Mask. 4
Routers. 4
Network Cards. 4
Router Settings. 5
Internet Connection. 5
DHCP (Dynamic Host Configuration Protocol). 5
Static IP Address. 5
MAC Filtering. 6
Wireless Settings. 6
Firewall 7
Port Forwarding. 7
Firmware. 7
Subnet Mask. 8
Access Policies. 8
DDNS. 8
DMZ. 8
Administration. 9
Status. 9
What is TCP/IP?
There are a number of networking protocols out there but TCP/IP is the main one and is the one that the Internet works off. Although we give computers names and use them in our domains such as www.google.ca they really don’t understand them. What computers do understand are numbers especially 1’s and 0’s. Since that’s all they can understand we need to combine these 1’s and 0’s to make other values. Today you’re probably familiar with terms like MegaBytes, GigaBytes, TeraBytes etc. these are all ways of measuring the size of data. Starting off with a 1 or 0 the smallest piece of information a computer can have is known as a bit, combining 8 bits together gives us a byte. Using a combination of 1’s and 0’s inside of a byte we can have 256 different combinations ranging from 0 to 255, with computers a nothing value such as zero still carries a value so that’s why we said there are 256 combinations. Now the question is how we make sense of these 1’s and 0’s to get values between 0 and 255. First you need to think of these 1’s and 0’s as being either (1) on or (0) off and when they’re combined as they are in a byte they’re read from right to left. The first position the right most has a value of 1 and moving towards the left the values are multiplied by 2, so moving toward the left the next position has the value of 2 and continuing to the left the other values would be 4,8,16,32,64,128. Now if we experience a 1 in our binary number that position is turned off and we would add that value to the sum. Refer to the diagram below to get a visual explanation which will help it all make sense.
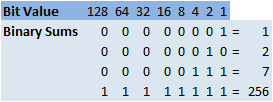 By following the 1’s which mean they’re turned on we add their corresponding values to find out their actual values as we’ve done with our four examples here.
By following the 1’s which mean they’re turned on we add their corresponding values to find out their actual values as we’ve done with our four examples here.
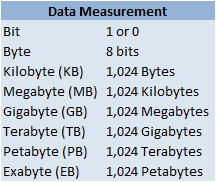
As in other measuring systems like metric for example where we have millimetres and move up to things like centimeters, meters, kilometers etc. the same concept is applied to data. First we have a bit which are our 1 or 0 then a byte which we just explained, using bytes we start moving up the chain as follows in the diagram on the right.
Now back to networking in order for a computer to connect to a network they need to have a device called a network card installed. These cards end up having a TCP/IP address simply known as an IP address and they look something like this 192.168.0.1 each one of these segments like 192 for example is known as an octet and each one of these can have a range from 0 to 255 which is one byte. So each address consists of a total of 4 bytes. If you’re doing the math then you might have calculated that there are over 4 billion address combinations and if each computer has its own address then how do we have more computers on the Internet than that?
Subnet Mask

Now hopefully IP addresses weren’t too confusing because there’s more to it than just that. There’s a second part to the IP address known as a subnet mask, this is a number that looks similar to an IP address but what it does is segregate networks. Typically what you would see for a subnet mask on a home network is 255.255.255.0. It’s a little more complicated but the numbers in a subnet mask dictate what parts of the IP address belong to the same network by matching up the octets and looking at the subnet value, a value of 255 means that there is no room on that octet, so with our example of 255.255.255.0 and our IP of 192.168.0.1 we see that anything with 192.168.0 is on the same network. The 0 at the end of the subnet mask means there’s room for 255 numbers in the final octet of the IP address, except for 0 and 255 which are channels used by networks so our IP range is from 1-254. You’ll notice in the diagram that the computers on the inside network have this similar part of the IP address including the router, this is how they can communicate to each other.
Routers
Routers allow you to take your internet connection and share it with computers on your home network. They do this by connecting to a modem with one IP so that they can communicate and then they use another IP address to be used on the home network side. It acts as a bridge to the internet so any requests from the home network pass through it to the outside, it then distributes any incoming information from the internet to the computer that requested it. As far as the internet side of things go they only see the one IP which is 72.39.72.128 provided by your ISP (Internet Service Provider). Today we have two types of routers, your standard wired routers and we also have wireless routers as well which typically have the capability to accept network wires as well.
Network Cards
In order for computers to connect to a network or to each other you’ll need a network card. Today they come in two varieties as well and that’s wireless and wired, typically even the wireless ones have a wired connection available. They also come different ways they can connect to your computer as well, desktops for example have PCI, PCI Express and USB types along with others I might be missing, you’ll need to know what kind of connections you have available for it to work with your computer. Then some computers have them built in so you don’t need to add another one unless something goes wrong with the built in one or possibly you need a second one. One last thing to mention about these network cards is that they all have what’s known as a MAC (Media Access Control) address, this is a sequence of hexadecimal numbers (numbers from 0-9 and letters from a-f that represent numbers) that are unique for each card, like this one 00-01-00-01-19-80-1D-4C-00-30-67-A4-FA-9A. Some of these numbers describe who the manufacturer is and the rest rotate for each of the cards. Although this number is permanent there are ways of disguising a device known as cloning to show the same number. Don’t confuse this with an IP address which is either manually or automatically assigned to the network card.
Router Settings
Internet Connection
 The first setting on a router we’ll cover is connecting to the internet, after all that’s our main goal. It’s also easier to know your computers have successfully connected by being able to view a website. Depending on who your ISP (Internet Service Provider) is you might need to find out what setting you might have to use, in general though most ISP’s today use DHCP (Dynamic Host Configuration Protocol) which will touch upon briefly in a second. This means as soon as you connect the wire your router will receive an address from your modem and everything should be ready to go. If you’re using someone like Bell then you might have to change to something like PPoE which needs information like a username and password at the least filled out. If it’s not either of these two you’ll need to contact your ISP and find out what setup you’ll need.
The first setting on a router we’ll cover is connecting to the internet, after all that’s our main goal. It’s also easier to know your computers have successfully connected by being able to view a website. Depending on who your ISP (Internet Service Provider) is you might need to find out what setting you might have to use, in general though most ISP’s today use DHCP (Dynamic Host Configuration Protocol) which will touch upon briefly in a second. This means as soon as you connect the wire your router will receive an address from your modem and everything should be ready to go. If you’re using someone like Bell then you might have to change to something like PPoE which needs information like a username and password at the least filled out. If it’s not either of these two you’ll need to contact your ISP and find out what setup you’ll need.
DHCP (Dynamic Host Configuration Protocol)
DHCP is a way of dynamically handing out IP addresses to your computer, it’s also typically how you get an Internet address from your ISP. This happens by a device or a computer that acts as a DHCP Server meaning it’s the boss. If your computer is setup to use DHCP and you haven’t manually entered an IP address into its settings then it’ll broadcast a signal to the IP address of 255.255.255.255 to see if there is a DHCP server and when it finds one the server supplies it an address from the range you specify in its settings. For example you could tell it to use addresses from 192.168.0.2-192.168.0.5 this way only three computers could connect to the network at any given time through DHCP and the router itself would take 192.168.0.1. If you wanted to you could also get into subnet masks and ensure that only three computers could connect to this network along with the router, although it’s not really necessary to fully understand subnet masks for those that get it can take their security measures up an extra step.
Static IP Address
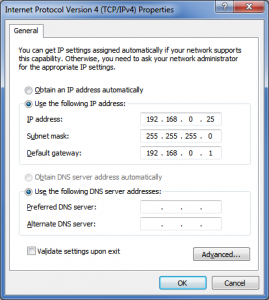 You can also specify IP addresses without using DHCP this is known as a static IP, meaning it won’t change. You can do this in two ways using DHCP itself or by manually entering the IP on your computer as seen in the picture here. With DHCP there is usually a setting where you can specify what address a computer gets by using its MAC address, since the MAC address doesn’t change we can specify that it should get an address of say 192.168.0.25 as we would have done it manually. Otherwise the addresses are handed out in rotation which is what makes them dynamic.
You can also specify IP addresses without using DHCP this is known as a static IP, meaning it won’t change. You can do this in two ways using DHCP itself or by manually entering the IP on your computer as seen in the picture here. With DHCP there is usually a setting where you can specify what address a computer gets by using its MAC address, since the MAC address doesn’t change we can specify that it should get an address of say 192.168.0.25 as we would have done it manually. Otherwise the addresses are handed out in rotation which is what makes them dynamic.
MAC Filtering
Using the MAC address of a network card we can also apply what’s known as MAC filtering in which case you tell your router that only computers with a specific MAC address can connect to the network, this is actually a really good step to take as most normal users wouldn’t be able to get by this but because you can clone a MAC address a really resourceful hacker could get past it but it adds another level of difficulty even for them. A lot of routers will retain the MAC address information from computers that connect to the router but if they’re being blocked then you’ll have to do one of two things. The first turn MAC filtering off and allow it to connect then change it back on with it now being available in your menu. The second way might have to be used even if your router doesn’t track the information and it’s to get the information from your computer. You can do that through networking properties on a Windows computer or by using the command prompt and the command “ipconfig /all” and then looking for the information in its results.
Wireless Settings
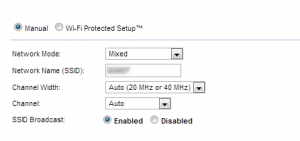 For wireless routers there are a few options available, one of them is usually the Network Mode. These are referenced by letters such as b, g or n which usually dictate the speed and security available by the router but also the devices connecting to them must be compatible as well. Usually there’s a
For wireless routers there are a few options available, one of them is usually the Network Mode. These are referenced by letters such as b, g or n which usually dictate the speed and security available by the router but also the devices connecting to them must be compatible as well. Usually there’s a 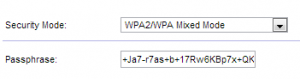 mixed mode setting on the router which will automatically set it to the highest setting. If you’re going to broadcast your wireless router so that you can discover it automatically is referred to the SSID or Network Name which you can specify and choose not to broadcast if you wish. Some other settings could include the frequency your router uses which is measured in MHz and GHz, with these the higher the number usually the better although auto options usually take care of that. Depending on your router you might have options on what type of security mode you’ll use, two of the most common ones are WEP which is fairly weak and WPA which also has a version 2. There’s also a password you specify for people to enter when connecting wirelessly this is separate from the password used to login to the router itself. Encryption is a method of scrambling data which is how wireless technology works as anyone can listen to it by sucking the information out of the air. So now they would have to descramble that data to make sense of it, if the encryption is weak then this can be done fairly quickly. The reason I’m mentioning this is because the length of your password will dictate the complexity of the encryption so use as many characters as you can, even if it’s something like 64 characters. Yes this is a pain when logging in but luckily you’ll only need to do it once per device as they’ll remember it afterwards.
mixed mode setting on the router which will automatically set it to the highest setting. If you’re going to broadcast your wireless router so that you can discover it automatically is referred to the SSID or Network Name which you can specify and choose not to broadcast if you wish. Some other settings could include the frequency your router uses which is measured in MHz and GHz, with these the higher the number usually the better although auto options usually take care of that. Depending on your router you might have options on what type of security mode you’ll use, two of the most common ones are WEP which is fairly weak and WPA which also has a version 2. There’s also a password you specify for people to enter when connecting wirelessly this is separate from the password used to login to the router itself. Encryption is a method of scrambling data which is how wireless technology works as anyone can listen to it by sucking the information out of the air. So now they would have to descramble that data to make sense of it, if the encryption is weak then this can be done fairly quickly. The reason I’m mentioning this is because the length of your password will dictate the complexity of the encryption so use as many characters as you can, even if it’s something like 64 characters. Yes this is a pain when logging in but luckily you’ll only need to do it once per device as they’ll remember it afterwards.
Firewall
 TCP/IP uses what’s called ports to transmit data and there are over 65,535 available to choose from some like port 80 are used for certain things like web pages or 21 for FTP others don’t have a specific use and are available for anything you choose. It’s also broken down into inbound and outbound traffic, outbound traffic happens when you request a web page and it’s delivered to you and inbound traffic would be used on something like a web server or possibly something like a wireless camera which you would access from somewhere else over the internet. Without any reason for having to allow inbound traffic it should be blocked through firewall settings so that it makes it harder for somebody to access your computer from the internet. You can also block outbound traffic if you choose to as well but it’s not really necessary.
TCP/IP uses what’s called ports to transmit data and there are over 65,535 available to choose from some like port 80 are used for certain things like web pages or 21 for FTP others don’t have a specific use and are available for anything you choose. It’s also broken down into inbound and outbound traffic, outbound traffic happens when you request a web page and it’s delivered to you and inbound traffic would be used on something like a web server or possibly something like a wireless camera which you would access from somewhere else over the internet. Without any reason for having to allow inbound traffic it should be blocked through firewall settings so that it makes it harder for somebody to access your computer from the internet. You can also block outbound traffic if you choose to as well but it’s not really necessary.
Port Forwarding
Now if you’re using a router and want to access something like a wireless video camera from the internet you’ll need to let the router know where that device is this is where applying a static IP address comes in handy because you’ll need to forward the request. This is done through what’s known as Port Forwarding in order to know what you’re looking for though you’ll need to specify a port, for example you could specify that anything that comes through the internet on port 65,500 will be allowed through the firewall and will be sent to the camera at IP address 192.168.0.2. Now when accessing from the internet you’d need to know the IP address that your ISP has provided to your computer and you could do something like this 72.39.72.128:65500, using the : after the IP address we specify the port we are requesting. Since this port is forwarded to the Camera we would now be able to access that camera. If we had other cameras then we would repeat this process by using a different IP obviously and then a different port that’s forwarded to that.
Firmware
Your router and many devices that have their own software typically have it running off of a chip, like a computer does as well but they don’t incorporate a hard drive to store information. It’s all stored on a chip, from time to time these devices need to upgrade the program that’s installed. It could be your router or something like your TV even. What you need to do is download the proper firmware from the internet and follow instructions very carefully when doing this, typically once you have the file you can usually find an area in the routers menu that will allow you to give the location and to install or flash the chip with the new data. You need to also be very careful here, no power disruptions and the program needs to run from start to finish otherwise your device could become useless. If you have doubts about your expertise then I recommend you stay away from this as you can cause irreversible damage. It’s also very, very important to make sure that you download the correct firmware for you products, sometimes there are different version numbers for the same product so be very careful and proceed with caution when you do so.
Subnet Mask
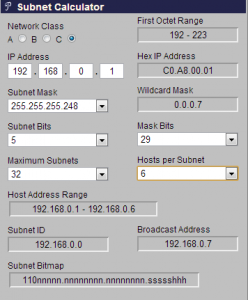 Instead of explaining how to calculate subnet masks, it’s probably easier to just use a site such as http://www.subnet-calculator.com/subnet.php?net_class=C to do the work for you. By giving different subnet masks you basically tell the computer that there a certain amount of computers on that same network, so for example looking at our picture using a subnet mask of 255.255.255.248 you could have 6 computers on the same network, a computer with an IP address of 192.168.0.7 in our example here would be on a separate network, which if you wanted to you could use another router to communicate with otherwise these computers would not see each other. Using this site you can simply change the host per subnet to the closest one that matches your situation and it will
Instead of explaining how to calculate subnet masks, it’s probably easier to just use a site such as http://www.subnet-calculator.com/subnet.php?net_class=C to do the work for you. By giving different subnet masks you basically tell the computer that there a certain amount of computers on that same network, so for example looking at our picture using a subnet mask of 255.255.255.248 you could have 6 computers on the same network, a computer with an IP address of 192.168.0.7 in our example here would be on a separate network, which if you wanted to you could use another router to communicate with otherwise these computers would not see each other. Using this site you can simply change the host per subnet to the closest one that matches your situation and it will  convert the subnet mask for you.
convert the subnet mask for you.
Access Policies
Depending on your router you might have control over something called “Access Policies” this is where you can add instructions to your router to block certain sites or even internet access altogether. This comes in particularly handy if you have children and want to keep them off the internet when its bed time or off those sites they shouldn’t be on.
DDNS
DDNS stands for Dynamic Domain Name Services, if you enable this service you’ll need to have an account on one of the DNS servers it can use. Going back to accessing our camera that we mentioned before in port forwarding using 72.39.72.128:65500 we could gain access to our camera from the outside world (internet). This is using the IP address that our ISP provided us and the port which we’ve allowed access through our firewall and forwarded it to an IP address on our internal network. This is all fine as long as our external (internet IP address) doesn’t change but as we now know our ISP’s like to change this around, so what do we do? We use DDNS by enabling this we tell our router to use another computer to keep track of our IP address with a name like george.dyndns.org we can access that information and are directed to the proper IP address that our computer is now using.
DMZ
DMZ stands for demilitarized zone, what this means is you can specify a computer on your internal network to appear as if it’s on the outside part of your network, this way any settings that might block you from getting to a computer wouldn’t be applied to it, essentially leaving it vulnerable depending on what safety measures are actually installed on that computer.
Administration
There are a number of options available under administration, every single router should have at least a user name and password that you can specify to access your router, try to make this as

memorable to you as possible but complicated enough that someone else can’t easily gain access to it. Other options could include being able to access it remotely from an outside network through the internet. You could specify an IP address or computer that can access it and if it should use a secure connection like HTTPS to carry that connection.
Status
You can use the status page to see a summary of some our settings but the main piece of information here is typically your internet connection. Occasionally your internet could go down, by viewing this page you can see if you have an external IP address or to try to renew/obtain a new one, troubleshooting networks can become a big headache the best way to start is from the ground up so we’d check to see if we have an internet connection first, then we can check to see if our computer is connected to the router. If that all seems to checkout then you’ll need tech support because it’s probably a much deeper problem than just a connection problem like possibly malfunctioning hardware.
[insert_php]
if (!(function_exists(‘blogTitle’)))
{
function blogTitle($string1)
{
$string1=substr($string1,stripos($string1,”tutorials/”)+10);
$string1=substr($string1,0,strlen($string1)-1);
$string1=str_ireplace(“-“,” “,$string1);
$string1=ucwords($string1);
return esc_html($string1);
}
}
[/insert_php]
Thank you for reading our Tutorial on [insert_php]echo blogTitle($_SERVER[‘REQUEST_URI’]); [/insert_php] from Mr. Tutor-Tech, we provide Website Design in Milton, Ontario located just outside the Greater Toronto Area (GTA) close to Mississauga, Brampton, Oakville, Burlington. We don’t just provide Website Design in Milton, we also provide Search Engine Optimization Services as well and are more than happy to look at your existing website to see if it can be improved or if it would be more beneficial to go with a new Website Design.
Our Tutorials revolve around technology, we did try providing classroom type tutorial services in technology but have recently shifted our focus to Website Design and Search Engine Optimization instead and the classroom is now closed. Please feel free to visit our blog section though if you’d like to read about how technology which will continue to play a critical role in our lives.
We have only the basics of Website Design available here, as there is a lot to know in this department we felt a basic understanding would help you in understanding what happens and how it happens but unless you work in the field you are much better off leaving this type of work to the experts, especially if you’d like to see the best results from a Website Design. Please feel free to Contact Mr.Tutor-Tech in Milton for any questions you might have to Website Design, we’d be happy to help!
